So WPAD requests happen from most systems all the time. But most of us do not realize it. And a lot of people do not seem to care. However if you do a search for WPAD attack you will find multiple articles that discuss varying types of attacks. If after reading those and you are not concerned about your users and their data. As well as the companies data. Then maybe this post is not for you.
Below is a few good articles that talk about some of the exploits and how to find it in some cases.
https://www.extrahop.com/company/blog/2017/detect-wpad-exploit/
https://googleprojectzero.blogspot.com/2017/12/apacolypse-now-exploiting-windows-10-in_18.html
I am not going to write an article about how the attack works as there are plenty of these articles out there. Fact is WPAD, ISATAP, and LLMNR have been used for Man in the middle type attacks. And it is a common well known attack vector. So you should be concerned. Personally I have tried to get rid of all 3 on my personal machines. And have worked with several companies to decrease there presence on their networks.
For larger environments, I am more concerned with how to fix the problem. And how to find stragglers. As well as how to spot the attack if I can’t stop wpad requests. There are lots of articles that talk about removing WPAD or stopping WPAD. Many of them talk about using a host file. And we tried that and it does work but keeping up with the host file is a management challenge. We have also found that it does not stop all the methods that proxy auto configuration uses. You have to realize that a request for the PAC file or the script to setup the proxy can be done by DNS, DHCP or with in an http request. This means that just doing a host file does not stop all the methods of attack.
For me I have found that disabling the IPhlpsvc, and the winhttp-proxy service has stopped this the best. But how do I verify that it actually stopped. And that stragglers are not out there. This is where DNS monitoring via Logs, or Network traffic analysis (NTA) with a tool like Extrahop becomes invaluable. The problem with DNS logs is that without some sort of log aggregator it is hard to keep up with. And even with an aggregator it is possible during high traffic times the logs might not be ingested fast enough. So some data may be lost. With NTA this is less likely. So I tend to want to use NTA over a log aggregator\parser.
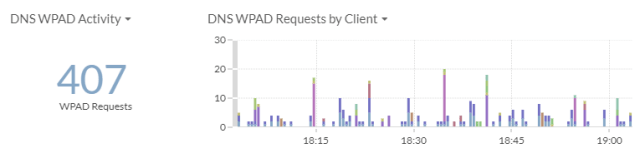
Here you can see there was 407 requests for wpad. With Extrahop it is possible to drill down to see what clients are making the requests and then work to fix them.
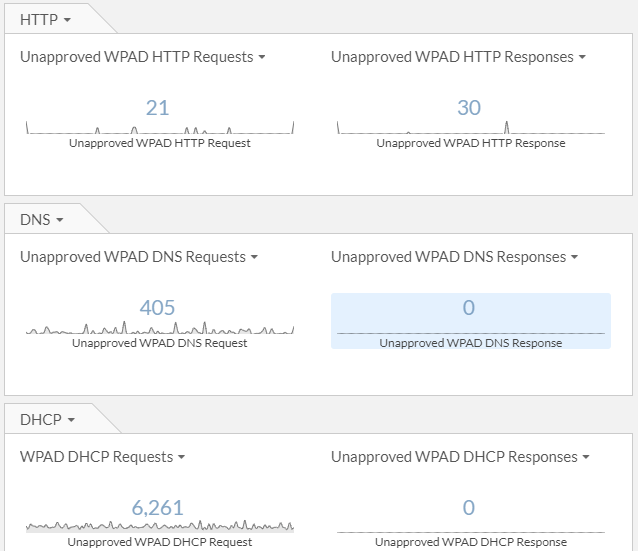
What is even more concerning is responses to WPAD requests. If you can’t stop them, or it takes time to stop them due to change control requirements. At least I want to know what is responding to those requests. As these may be an indication of a man in the middle attack especially if you do not use WPAD. So below is a chart from Extrahop that allows me to see how many requests and how many responses Extrahop is seeing in my environment.
Hope this helps someone find and remove WPAD from their environment.

Great article Mitch! Yes, it’s pretty scary to think that a rogue PC on the network could end up handling/proxying all of your internet-bound traffic!